Chapter 5 ~ How Privacy and Security Works
⬆ Shiftrefresh Shift-Refresh this page to see the most up-to-date instructions.
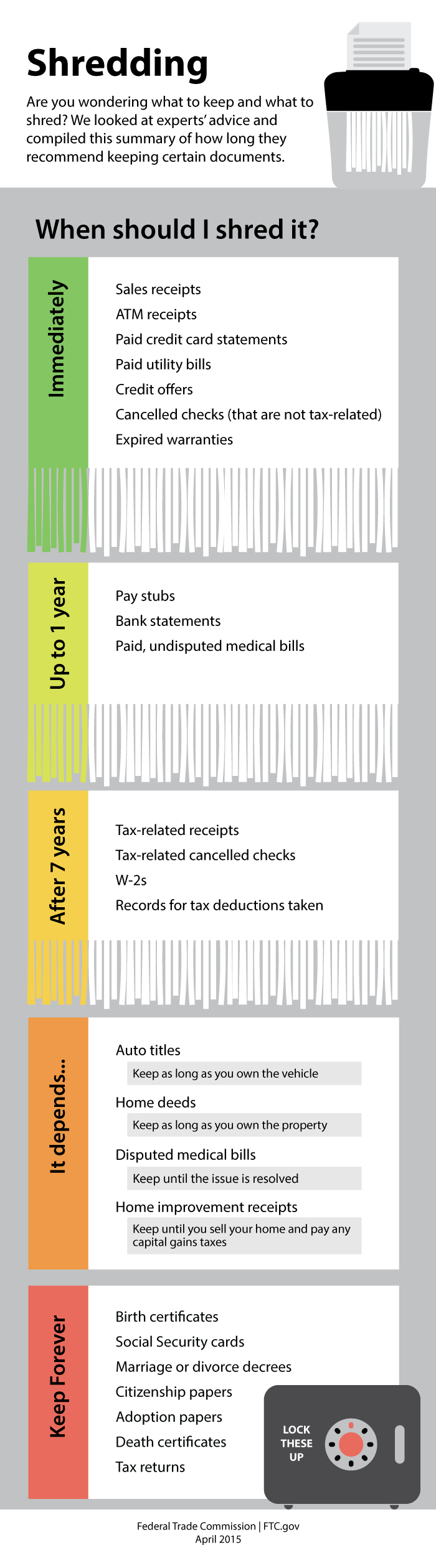
When Facebook added open graph sharing of user data to its application in 2010, it allowed third-party vendors like Cambridge Analytica (UK) to scrape personal user data so it could target their news feeds with political ads. In 2011, the USA Federal Trade Commission (FTC) required Facebook to get the user's consent before sharing that data. However, that didn't happen. Consequently, 87 million users were targeted by Cambridge Analytica with misleading political ads paid for by politicians, which experts say unfairly swayed many presidential elections around the world.
How do we ensure our privacy and security online when companies and governments may not care?
These kinds of issues and new regulations arise when companies are not fully invested in keeping our personal data safe (learn more from the FTC's Data Breach Responses: a guide for businesses in the USA). In addition, most people are not careful with their data.
In this chapter, you'll explore malicious acts, privacy, security, and prevention topics while working together in a collaborative document. In discussion, you'll tell us how you personally tightened up your digital footprint based on recommendations from Consumer Reports.
This chapter's skills and discussion will take between 4 and 12 hours to complete.
In this lesson, you'll be contributing to the development of a Cybersecurity Manual by writing about a single topic, making recommendations to your classmates, and implementing their recommendations. The goal is to write and format the document so it has zero mistakes!
Read the detailed instructions provided in the Collaboration document (large green buttons in step 5.2, below) before you begin.
5.1 Research a cybersecurity topic.
5.1.1 Research, write, and illustrate.
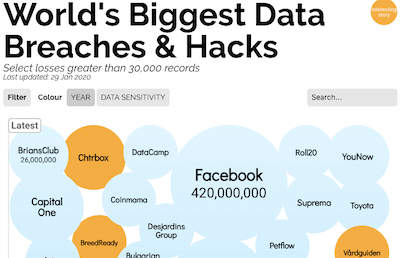
- Explore the
World's Biggest Data Breaches & Hacks infographic (2004 to present).
Do you see an interesting topic you'd like to explore further?
Use links in the infographic to learn more about a malware incident.
- Choose one malware or cybersecurity term from the list below:
To avoid duplicate topics, do not write about a topic until you view the collab doc in step 5.2...!- Acoustic Cryptanalysis
- Ad Fraud and Malvertising
- Advanced Persistent Threats (APT)
- AI Transformers
- APT Side Hustle or Privateering
- Astroturf
- ATM Skimming
- Backdoor, Exploit
- Bluejacking
- Bots, Botnets, Bot Master, Bot Herder
- Browser Hijack, Session Hijacking
- Brute Force attack
- Bug
- Catfishing Cloaking
- Click Bait, Engagement Bait, Malvertising
- Credential Stuffing
- Cross-site Scripting (XSS)
- Cryptojacking
- Cyberflashing
- Cyberwarfare
- Dark Patterns
- Data Breach and Spillage
- Deep Fake
- Dedicated Denial of Service Attack (DDoS)
- Differential Fault Analysis Attack
- Domain Fluxing
- Domain Spoofing
- Doxing
- Drive-by Downloads
- Electromagnetic attack
- Encrypting, Hashing, Public Key Encryption, Private Key
- Erasure Coding
- Evil Twin and Rogue Access Point
- False Flag
- Fileless Malware
- Firewall
- Form Grabbing
- Geotagging, geolocation
- Ghosting
- Grayware
- Hacker, White Hat Hacker, Black Hat Hacker, Cracker
- Intrusion Detection
- Injection Attack
- Juice Jacking
- Keylogging
- Logic Bomb
- MaaS (Malware as a Service)
- Man-in-the-Middle attacks
- NAND Mirroring
- Network Telescope
- Pharming
- Phishing, Spear Phishing, Whaling, Angler-phishing
- Rainbow Table Attack
- RAM Scraper
- Ransomware and Crypto-Malware
- Robocall
- Rogue Security Software
- Remote Access Trojan (RAT)
- Rootkit, Bootkit, Rooting
- Smishing
- Sniffing, Password Sniffing, Packet Sniffing
- Social Engineering, Pretexting
- Sockpuppet
- Spam and Blacklisting
- Spoofing
- Spyware, Stalkerware, and Snooping (sound, video, webcam)
- Stalkerware
- Stingray
- Super-cookies, Evercookies, Zombie Cookies, Sidejacking
- SYN Flooding
- Tailgating, Shoulder Surfing, and Dumpster diving
- Threat, threat actor, threat agent
- Traffic light protocol
- Trojan Horses
- Typosquatting
- Virus, Macro Virus
- Vishing
- Vulnerability, vulnerability assessment and management
- War Dialing
- Web Skimmers
- Whitelist, Blacklist
- Watering Hole attack
- Worms
- Zero-Day Exploit
- Zombie computer
- Zoombombing
- Launch a word processing document and save the file as How Privacy and Security Works First and Last name.
Summarize your chosen topic in 300 words or more, written in the third-person style. Include:
- A definition of the term.
- A summary of an actual case where the concept was used.
- A solution to the problem, such as how software developers could prevent the problem, or how users could prevent or fix the problem.
- Apply the > Normal style to your paragraph (do not add indents or any other formatting).
- Cite all sources by hyperlinking their titles in a sentence in the paragraph.
- Bold key concept names (not long phrases).
- Illustrate the concept you wrote about to show how it works.
- Place your cursor at the start of your paragraph.
- Choose > > Search the Web.
- Search for a diagram, chart, or photo that illustrates the concept you wrote about. simple decorative images are not allowed. Illustrations must include written information, such as how the technology works.
- Select your choice and click the blue Insert button at the bottom of the search pane. Wait patiently while the image loads onto the page.
- Review it to ensure it relates; it is very hard to tell from the small search pane. If necessary, search again from a different browser tab and > > By URL.
- Click the image to access the text-wrapping menu and blue resizing handles. Click the middle text-wrapping option. Use the blue handles and shift key simultaneously to proportionally reduce or enlarge the image, so it is no taller than the paragraph you wrote about.
- Capture the bibliographic data for each source of research and illustration using your Bibliography tool.
5.1.2 Save and submit your file.
Save your document as a PDF file. This is the primary file you will submit in Canvas.
- > PDF/XPS. Save the file to your CS 101 folder on the hard drive.
Each assignment must be submitted before the Due date and time as specified on the Canvas Home tab. The Available Until date and time constitutes a grace period, which can be used in an emergency, or if you are ill (it cannot be used for every assignment). Students who submit using the Available Until date may incur score reduction. Students on a DAS Flexibility Contract: there is no need to notify the instructor. All of your Available Until dates will be set to 72 hours past the Due Date, which can be used up to 3 times. Abuse of the Flexibility Contract will be reported to DAS.
- Click on the Canvas Home button and scroll down to the Ch 5 ~ How Privacy and Security Works assignment. Click the assignment link.
- Upload the PDF file you created (not the entire Collaboration document). Confirm that it uploaded.
 Check the TurnItIn Report for plagiarized phrases and sentences.
Review how to use TurnItIn.
Edit or add quote marks in your original file to ensure the second draft of the file will pass the TurnItIn inspection.
Resave the PDF file.
Upload the newer version in the assignment's Submission Details screen.
If you made revisions based on the TurnItIn report, then make those same changes to the collaboration document.
Check the TurnItIn Report for plagiarized phrases and sentences.
Review how to use TurnItIn.
Edit or add quote marks in your original file to ensure the second draft of the file will pass the TurnItIn inspection.
Resave the PDF file.
Upload the newer version in the assignment's Submission Details screen.
If you made revisions based on the TurnItIn report, then make those same changes to the collaboration document.- Within 3 days of submission, be on the lookout for Rubric feedback and Comments from the TA and Instructor.
- Ask questions about the score and feedback in the assignment's Commenting box.
5.2 Collaborate in a cybersecurity manual.
Now that your contribution is written and edited, add it to the Cybersecurity Manual collaboration document. Login to your OSU Google account then open your section's collaboration file:
Summer 2024 Cybersecurity Manual
Winter 2024 Cybersecurity Manual
Follow instructions in the file to complete the pasting of your writing and illustration. If your illustration did not paste, then use the procedure in step 5.1.7 to insert it into the collaboration document.
5.3 Review
You and your classmates will take on the role of editor to help improve the document you did not already contribute to.
- Review the Cybersecurity Manual collaboration document.
Read the entire document (even if not everyone has collaborated yet) and
> Comments where appropriate, to suggest improvements to:
- Grammar
- Spelling
- Formatting of styles. If added an indent; remove it.
- Writing consistency (all entries are written in the third-person style with hyperlinked titles)
- Illustration formatting. None of the illustrations should be taller than their paragraphs and text should wrap on the left or right.
- Bibliography placement and consistency (each entry should be in the Bibliography section (last section of the document) and use the same order of author, title, publisher, year, and URL).
- When you receive comments via email related to your paragraph, go back to the collaboration document to make the revisions suggested by your classmates.
- Click the Checkmark button for each comment you resolve.
5.4 Extra Credit Designs.
To improve the design of the collaboration document, add one of the following components to the document (if they have all been implemented, you can implement future extra credit options later):
- Add a Table of Contents.
Ideally, this option is completed after the deadline, so that all entries are provided beforehand.- Under the instructions on page 1 of the collaboration document, Insert > Table of Contents.
- From the resulting list, replace the redundant headings in the first two or three lines with Table of Contents and apply Heading 2.
- Select the list under the new heading and change the line spacing to Single and remove the space after so the list doesn't take up more than 2 pages.
- Leave a comment in the Canvas Assignment Details page letting the Instructor and TAs know you completed this option.
- Add a footer with page numbering, counting, and line.
- From the menu, choose Footer.
- Place the cursor in that new footer area and from the menu, choose Page Numbers and
the option that starts numbering on page two (so the Table of Contents cover page isn't numbered).

- Double-click into the new footer and place the cursor after the number.
Type a slash / or vertical bar |.
From the menu's Page Numbers option, choose the Page Count option.

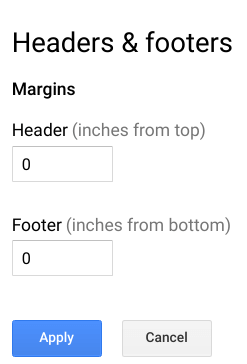
- From the Footer's link, update the Footer margin to 0.
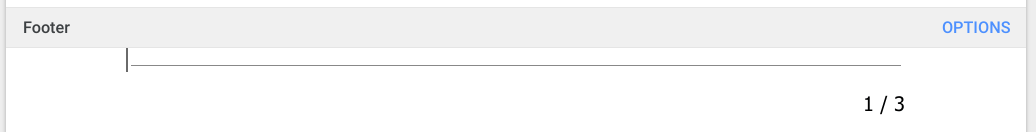
- From the menu, choose Horizontal Line. The footer should look like this now:
- Leave a comment in the Canvas Assignment Details page letting the Instructor and TAs know you completed this option.
- From the menu, choose Footer.
- Sort the bibliography alphabetically.
Ideally, this option is completed after the deadline, so that all entries are provided beforehand.- Remove all quotation marks from the bibliography entries.
- Copy the entire list to another document when logged into your own personal Google Account or a Microsoft Word document.
- If using Google Docs, use the menu > Get Addons and search for Doc Tools by Ablebits. Add it. Select all of the entries and from the , choose Sort A to Z.
- If using Microsoft Word for sorting, select the list and apply the tab's AZ↓ button. You many also need to sort the text by paragraph and choose in ascending order. Note that when using Word on Mac, the sorted list will not paste properly into the Google Doc...so proceed with caution.
- Copy the newly-sorted list. Select the old list in the collaboration document and paste the new entries to replace the old list.
- Leave a comment in the Canvas Assignment Details page letting the Instructor and TAs know you completed this option.
If a classmate attempted to complete one of the three options above but did not finalize it, then you may complete it to earn credit.
5.5 Verify your work.
From the Canvas Home tab, click the Ch 5 ~ How Privacy and Security Works assignment. Scroll to the bottom to see the Rubric. Compare your work to the Rubric to ensure you've included all paragraphs and reviewed/edited your work. The rubric is based on the following scoring criteria, which are based on the instructions above: Check off each criterion to confirm you've completed them before submitting the file.
- Paragraph, illustration, and bibliography entries are submitted as a single PDF file.
- Paragraph is free of plagiarism.
- Cybersecurity writing includes a definition, a summary of an actual case, a solution, is properly cited, and bold is applied to key concepts.
- Illustration provides information, relates to the scandal/term and has text-wrap applied to the right or left.
- Formatting, grammar, and spelling recommendations were implemented in the collaboration document.
- Bibliography entries are numbered, properly formatted, and consistent with other entries in the collaboration document.
If you helped complete the design of the document by implementing one of the extra credit options, then verify your work:
- Extra Credit: Table of contents includes automatic up-to-date page numbering for each heading 2 and 3 (excluding the instructions and title).
- Extra Credit: Footer includes a horizontal line, a page number, and a page count aligned to the right.
- Extra Credit: Bibliography is sorted alphabetically and no entries have quotation marks.